What is VPN detection, and how does it work?

Ever wondered how a website or network administrator can tell you’re using a virtual private network (VPN)? The answer lies in VPN detection tools. These tools look for VPN traffic patterns that don’t match regular internet activity on the network level.
This guide covers how VPN detection works, why it’s used, what the most common methods are, and the main limitations of these systems.
Why websites and networks detect VPNs
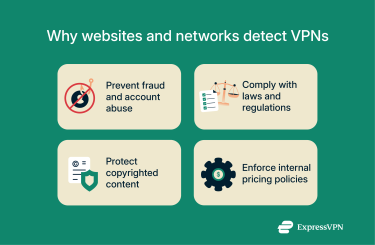 Platforms use VPN detection for a mix of practical, legal, and security reasons. These tools help prevent fraud or abuse and ensure compliance with local laws and licensing agreements.
Platforms use VPN detection for a mix of practical, legal, and security reasons. These tools help prevent fraud or abuse and ensure compliance with local laws and licensing agreements.
Preventing fraud and account abuse
Online services use VPN detection as part of their fraud prevention strategies to spot activity that doesn’t match normal user behavior. For instance, they may detect multiple logins from different countries within minutes, multiple transactions from different regions, or numerous account creations from the same device. This helps platforms reduce fake registrations, spam, and account takeovers, ultimately protecting legitimate users.
Blocking VPNs to protect copyrighted content
Licensing agreements and copyright regulations often define where content platforms can stream titles or make them available for download. These services detect VPN connections to ensure their content is only available in regions where it’s legally licensed. This helps them remain compliant with copyright laws and distribution rights.
Enforce internal pricing policies
Some online services use dynamic pricing, which means they adjust costs and promotional offers based on key factors, such as location, demand, supply, consumer behavior, and competition. These platforms often use VPN detection tools to understand where buyer intent comes from, maintain accurate market insights, and enforce internal pricing policies.
Identifying VPNs for compliance with laws and regulations
Some organizations face strict compliance and security requirements that may compel them to detect (and restrict) VPN use, like those operating in government, healthcare, or finance sectors. For example, payment processors often need to follow anti-fraud regulations that require them to flag or review transactions made through VPN connections.
How VPN detection works
VPN detection works by analyzing multiple layers of network traffic, along with location and device data. It combines various tools and techniques to determine whether a connection is coming from a VPN or a regular network.
Note: This information is for explanatory purposes only and is not intended to assist in evading detection.
Common techniques used by websites and ISPs
VPN detection can take many forms depending on who’s using it. Websites and apps often focus on where a connection appears to come from, while internet service providers (ISPs) and network providers look at how that connection behaves. The following are the main techniques used for identifying VPN traffic.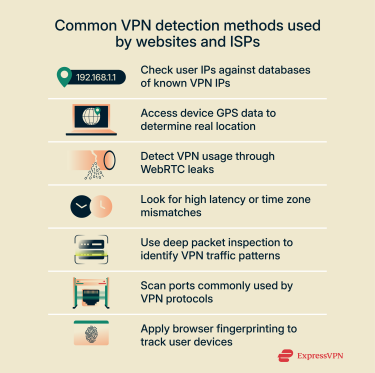
Detecting VPNs with IP address and database checks
Online platforms often detect or block VPN connections by checking the IP address against databases of IP addresses that VPNs use, which are maintained and updated by commercial detection services.
Financial platforms may also flag shared IP addresses when unusually large numbers of users connect from the same address, as this can indicate VPN usage. These checks are typically part of broader anti-fraud prevention systems.
Using GPS data to detect VPN use
Mobile apps with location-based features, like banking, ride-sharing, or streaming services, often use devices’ GPS data to determine a user’s location, instead of just relying on the user’s IP address to provide geolocation details. If the GPS location doesn’t match the VPN server’s region, the service might flag the connection as suspicious or restrict access.
Spotting VPN users through WebRTC leaks
Web Real-Time Communication (WebRTC) is a browser technology that allows direct peer-to-peer connections for video calls, voice chats, and file sharing. To work, it requires both participants to know each other’s IP addresses. However, these IP requests can sometimes bypass the VPN tunnel, causing a WebRTC leak that reveals your real IP to websites.
When this happens, an online service might receive your real IP through WebRTC while your visible connection still appears to come from the VPN server. This discrepancy can allow the platform to detect VPN usage.
Learn more: How to test your VPN and confirm it’s working
Using latency and time zone mismatches to reveal VPNs
Some platforms may look for timing patterns that don’t match normal user behavior. For example, a website might detect unusually high latency, suggesting the connection is routed from a distant location. It could also compare the browser’s time zone to the region associated with the IP address.
However, these checks are rarely reliable. Latency spikes can happen due to legitimate reasons, like network congestion, poor Wi-Fi signals, or hardware issues. Also, it’s easy to change the time zone on nearly any device, or the device can misreport it to the network.
Uncovering VPN traffic with deep packet inspection
ISPs and network administrators can’t decrypt VPN traffic, but they can often recognize it by its distinctive patterns. They typically do this using modern firewalls that support deep packet inspection (DPI), a method used for analyzing network traffic in real time.
DPI searches for patterns that stand out from normal internet activity, such as consistent packet sizes, evenly spaced transmission intervals, and long-lived encrypted sessions between the same endpoints. These characteristics suggest a VPN connection.
Detecting VPN protocols through port scanning
A port acts as a communication gateway between your device and the internet, and each VPN protocol typically uses specific ports to establish a connection. For instance, WireGuard uses User Datagram Protocol (UDP) port 51820 by default, whereas Internet Key Exchange version 2 (IKEv2) uses UDP ports 500 and 4500.
ISPs and network administrators can monitor or scan known VPN ports, and if a lot of encrypted traffic shows up on those ports, that raises a flag.
Using browser fingerprinting to spot VPN usage
Browser fingerprinting is a tracking technique that allows websites to generate a unique tracking identifier for each visitor based on their system and browser characteristics. The identifier contains various data, such as device type, time zone, operating system version, language settings, screen resolution, and installed browser extensions.
If a website detects the same fingerprint appearing under different IP addresses or locations within a short time, it can conclude that the user is likely connected through a VPN or other privacy tool that changes network identity while keeping the same device configuration.
Advanced VPN detection methods
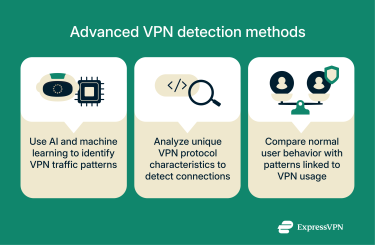 Some organizations go beyond basic VPN detection and use advanced analysis techniques to identify VPN usage. These can include AI-based systems, detailed VPN protocol fingerprinting, and behavioral monitoring tools.
Some organizations go beyond basic VPN detection and use advanced analysis techniques to identify VPN usage. These can include AI-based systems, detailed VPN protocol fingerprinting, and behavioral monitoring tools.
AI and machine learning in VPN detection
Modern VPN detection platforms can use AI and machine learning to better identify traffic patterns that traditional filters miss.
Engineers can train these models on network data that includes both normal and VPN traffic, allowing them to learn the differences between the two. The systems can then examine features like packet timing, routing paths, flow duration, and packet size patterns to decide whether a connection likely uses a VPN.
Protocol fingerprinting
Protocol fingerprinting focuses on recognizing the specific VPN protocol in use rather than just detecting that a VPN exists. Detection systems analyze unique traits, such as handshake behavior, header structure, and byte sequences, and compare them to known profiles for protocols like OpenVPN, WireGuard, or IKEv2.
This method allows for more precise identification, even when a VPN hides behind common ports or encryption methods.
Behavioral analysis of user activity
Some platforms may analyze how users behave while connected and look for inconsistencies between normal patterns and those typically linked to VPN usage. For example, they might flag simultaneous sessions from different regions or fast switching between countries.
They could also compare a user’s current activity to historical data from past sessions and identify behavior that doesn't align. For instance, if someone interacts with content specific to one country while logging in through an IP address from a different region.
Limitations of VPN detection
Even advanced VPN detection systems face practical and regulatory limits, including:
- False positives: Detection services can flag legitimate user behavior as suspicious, negatively affecting the experience of non-VPN users.
- Resource demands: Accurate, large-scale VPN detection requires continuous updates and significant processing power, which can be costly for some platforms.
- Regulatory constraints: Privacy laws may limit how much personal data organizations can collect and analyze, restricting the datasets they can use to cross-check for VPN activity.
Why no detection method is 100% accuraate
No detection approach can guarantee complete accuracy. Different VPN protocols, rotating server IP addresses, and obfuscation techniques can make identification difficult. Organizations must also strike a balance: monitoring too aggressively risks flagging legitimate users, while being too lenient can let VPN traffic go undetected.
FAQ: Common questions about VPN detection
How can I check if I’m using a VPN?
The easiest way is to use an online tool, like ExpressVPN’s IP address checker. If the displayed IP address, country, city, or internet service provider (ISP) differs from your actual location, you may have an active VPN connection. Check if there's a VPN app running in the background and disable it, or ask your system administrator if there's a network-wide VPN enabled.
Can websites tell if I’m on a VPN?
Yes, some websites can detect VPN connections using various techniques. For example, they may compare user IPs against databases of known VPN servers or use browser fingerprinting to see if the same device connects from multiple IP addresses. In some cases, browsers can also expose your real IP address to websites through Web Real-Time Communication (WebRTC) leaks, revealing your location even while you’re connected to a VPN.
Can my ISP detect a VPN?
Yes, your internet service provider (ISP) can often detect VPN usage by analyzing network traffic patterns. Advanced firewalls can recognize signatures belonging to VPN protocols, which help establish encrypted connections. ISPs may also monitor known VPN ports for activity because they allow your device to communicate with VPN servers.
Can a VPN be traced back to me?
This depends on the VPN’s no-logs policy and how websites use browser fingerprinting to track your device. If the VPN keeps IP or activity logs, that information could be shared with third parties and linked back to you.
Is VPN detection legal?
VPN detection is legal in most regions because it serves legitimate purposes. For example, websites may use it to prevent fraud and account abuse, while business, hotel, or school networks could implement it to manage bandwidth usage. However, since VPN detection tools may log personal information, they have to comply with applicable privacy and data protection regulations.
How do I test if my VPN is working properly?
You can check if your VPN is working by testing for leaks. For example, you can use a Web Real-Time Communication (WebRTC) leak test to see if your real IP is exposed to websites even while you’re connected to the VPN. You should also test for Domain Name System (DNS) leaks to make sure your web browsing isn’t visible to your internet service provider (ISP).
Can free VPNs be detected more easily?
Free VPNs may be detected more easily in some cases. This can happen because certain free services don’t include the same range of features or maintenance practices as paid options. For example, they might update server IP addresses less frequently or offer limited obfuscation, which normally makes VPN traffic harder to detect.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN