What is a virtual private cloud (VPC)?

A public cloud is a shared online infrastructure where an external provider manages resources and delivers them over the internet. A virtual private cloud (VPC) is a logically separated section within this environment.
VPCs play a vital role when it comes to protecting sensitive data, because they keep networks secure and isolated from the rest of the public cloud. They also offer benefits like scalability and pay-as-you-go pricing, combined with the control and isolation of a private data center.
This guide explains what a VPC is, how it isolates your network, and why it’s a standard tool for secure businesses.
Definition of a virtual private cloud
A VPC provides a private, isolated section within a public cloud. If you think of a public cloud provider as an apartment building, a VPC is a private apartment within that building. You have your own walls, your own key, and full control over who enters. Your resources run separately from everyone else’s.
The cloud provider (such as AWS, Google Cloud, or Microsoft Azure) manages the underlying physical infrastructure. This means you don’t have to buy, install, or maintain servers; you get the benefits of their infrastructure while keeping control over your private, cloud-based network.
In this secure space, you define the rules: you set the IP address ranges, create subnets, and configure firewalls and access control lists. You can run applications, store data, and host websites, and no one else can access these resources unless you grant permission.
This setup combines public cloud scalability and efficiency with private cloud security and control. You avoid the cost and work of building your own physical infrastructure, but you can still oversee your network. This is why VPCs are a standard for businesses in finance, healthcare, and any other fields that involve handling sensitive data.
How a virtual private cloud works
A functioning VPC relies on several core architectural components. These elements define your network's boundaries, organize its internal structure, and govern how data moves within it.
CIDR block (IP address range)
When setting up a VPC, you start by defining your own Classless Interdomain Routing (CIDR) block, which is an IP address range for your virtual network. This range is internal to the VPC (for example, 10.0.0.0/16) and isn’t reachable from the public internet. This block belongs exclusively to your VPC, and you have full control over how the network is segmented and used.
Subnets and routing tables
Next, you divide your large IP address range into smaller, manageable pieces called subnets. You can designate some subnets as public and others as private. A public subnet is for resources that need to connect to the internet, like a web server. A private subnet is for resources you want to keep isolated, like a database.
Every subnet has a routing table attached to it. This is a set of rules that acts as a traffic controller, telling data where it’s allowed to go. For example, a routing table for a private subnet might only permit traffic to and from your web server, blocking all other connections.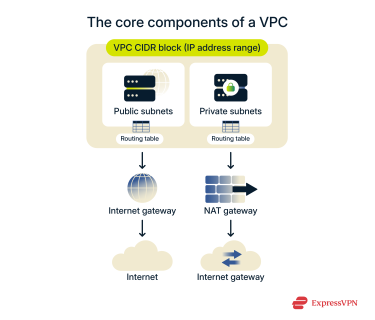
Internet and Network Address Translation (NAT) gateways
To get traffic in and out of your network, you use gateways. An internet gateway is a component you attach to your VPC to allow communication between your public subnets and the internet.
A NAT gateway is the service that lets resources in your private subnets (such as a database) initiate internet connections, for example, to download a security update. It does this without letting any unrequested traffic from the internet in.
VLAN (optional enhancement)
A virtual local area network (VLAN) allows you to create separate, isolated groups within a single physical network. For example, you could put your accounting department's computers in one VLAN and your marketing team's in another. Even if all the computers are plugged into the same physical hardware, the two virtual groups can't see or access each other.
This is similar to a subnet, which also divides a network at the IP level (Layer 3). While VLANs provide additional isolation in on-premises or hybrid setups, they’re optional in VPCs, and they’re not a core requirement across providers like AWS or Azure.
Key features of a VPC
A VPC provides a suite of networking tools that replicate a physical data center in a virtual environment. These include:
- Logical isolation: A VPC is a private environment dedicated to your account. It allows you to define your own IP address range (CIDR block) and segment the network using public and private subnets.
- Customizable network configuration: You have full control over routing tables and gateways. This includes the ability to define IP address ranges and set up internet gateways for public access or NAT gateways for secure outbound updates.
- Granular security controls: The system provides layered defense tools. You can use security groups to filter traffic at the instance level and network access control lists (NACLs) to filter traffic at the subnet level.
- Hybrid connectivity: VPCs support secure connections to on-premises infrastructure via site-to-site VPNs or dedicated lines like AWS Direct Connect or Azure ExpressRoute.
- Global reach: VPC geographic reach varies by provider; Google Cloud offers global VPCs natively, allowing resources to communicate across regions automatically. In contrast, AWS and Azure require peering or gateways to establish cross-region connectivity.
Differences between cloud types
When looking at different cloud types, the main questions are how much control you need and how much management you want to handle yourself.
VPC vs. private cloud vs. public cloud
You choose a cloud type based on your specific goals. A public cloud shares hardware among many users, while a private cloud uses dedicated hardware exclusive to your organization. A VPC sits in the middle: it provides the logical isolation of a private network on top of a public infrastructure.
The main differences come down to cost, control, security, and who manages the physical hardware.
Ownership and control
- Private cloud: A single-tenant environment where your organization owns the hardware or leases it from a provider who dedicates it all to you. You’re not sharing hardware.
- Public cloud: A multi-tenant environment where your workloads typically run on shared physical hardware with other customers, isolated through virtualization. Your resources can be reachable from the internet if configured that way, and they’re protected by provider-level network controls, such as security groups or firewalls, by default.
- VPC: Also multi-tenant, but adds a key layer of logical isolation. The cloud provider creates a private, locked-down “wall” around your resources, so you get full control over your virtual network, deciding exactly what gets in and what gets out.
Cost and resource allocation
- Private cloud: Requires a large upfront investment in servers. You also face ongoing costs for power, cooling, and staff. Adding capacity is typically slow and expensive.
- Public cloud and VPC: Both use a pay-as-you-go model. You only pay for what you use, and you can scale up in minutes. The cost is very similar, though a VPC might incur small extra charges for privacy-focused components, such as a NAT gateway.
Management and customization
- Private cloud: You’re responsible for everything: hardware maintenance, software updates, and daily management. This offers complete customization, right down to the specific hardware you choose to use.
- Public cloud and VPC: The provider handles all physical infrastructure, maintenance, and security patches, making management much easier. The main difference is that a VPC gives you far more control over the network configuration.
Security and performance
- Private cloud: Gives you physical isolation (since you own the hardware; no one else is on it). You also get dedicated, predictable performance because you’re the only user.
- Public cloud: Provides a secure but shared environment where your servers live on the same network as other customers’. The main risk comes from "noisy neighbors" (other customers on the same physical machine using substantial resources), which can slow your application down.
- VPC: Delivers the best of both worlds. You receive the provider's top-tier physical security combined with tenant isolation. Your network is private by default, reducing the risk of accidental data exposure. You also mitigate the "noisy neighbor" problem and can pay for a dedicated, high-speed connection straight from your office to your VPC.
When to choose each model
- Public cloud: Best for general-purpose applications where strict data isolation isn't the top priority; for example, a company blog, a development and test environment, or a simple website.
- Private cloud: Best for organizations with extreme security or regulatory demands, such as government agencies handling classified data or research labs that need to run on specific, custom-built hardware.
- VPC: The standard for securing business workloads in the public cloud. It's perfect for any application that handles sensitive data while remaining flexible and cost-effective. A classic example is an e-commerce site: you can run the public storefront in a public subnet while placing the customer database and payment processing system in an isolated private subnet.
VPC vs. VPN
This is a common point of confusion, but virtual private networks (VPNs) and VPCs do two completely different jobs. They don't replace each other; they work together.
A VPC is your private, isolated network in the cloud. A VPN is the secure transport from your computer that travels over the public internet and drops you off securely at the front door of your VPC.
VPNs create encrypted tunnels over the internet so you can safely access your private resources. The VPC is the private environment that isolates those resources from everyone else. You should use both for a complete security setup.
Read more: To learn more about VPNs and how they protect your privacy, read our full guides: What is a VPN? and VPN history: How virtual private networks evolved over time.
Benefits of using a virtual private cloud
A VPC gives you the control and security of a private cloud, but without the high cost and work of buying and managing your own hardware.
Enhanced security
A VPC minimizes your attack surface through isolation. By placing sensitive data in private subnets and using security groups to strictly limit access, you reduce the risk of data breaches. Leading cloud platforms provide tools to record activity and generate reports, while the provider manages security updates for the underlying physical infrastructure, ensuring the hardware remains patched and secure.
Cost efficiency and agility
You avoid the significant capital expense of buying and maintaining physical hardware. Instead, VPCs operate on a pay-as-you-go model; you can add or remove virtual machines on demand, and if you require additional processing power during peak hours, you can deploy these instances in minutes. This elasticity prevents you from over-provisioning hardware for "just in case" scenarios.
Regulatory compliance
A VPC can help you meet regulatory requirements by providing isolated, customizable networks within public clouds. This enables compliance with data privacy regulations like the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act of 1996 (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS), and minimizes public exposure risks through dedicated infrastructure.
Businesses gain full control over data residency and processing, and custom policies for encryption and classification further support granular security in regulated sectors.
VPCs also simplify audits by producing VPC flow logs, firewall logs, and control-plane logs and routing them to a central store for retention and review. Cloud-native tools like AWS Artifact provide control mappings and evidence collection, which can help you demonstrate alignment with Service Organization Control 2 (SOC 2) audits, International Organization for Standardization (ISO) 27001 controls, and the National Institute of Standards and Technology (NIST) SP 800-53 families covering access control, auditing, and system protection.
Common VPC use cases
You can use VPCs in many different ways, but they’re most common in scenarios that demand high security and the ability to scale.
Business continuity and disaster recovery
A VPC makes it easy to create backup systems. You can replicate your data and applications in another region (a provider’s data center in a different city or country, for example). If your primary site fails due to an outage, you can instantly switch over to the backup. This is much simpler and more affordable than building and maintaining your own separate disaster recovery site.
Application development and testing
You can create completely separate environments for your development, testing, and live ("prod") applications, all within the same VPC. By using different subnets, you can build a safe copy of your live setup to test new features. Your automated build and release processes can run inside this secure network, protecting your code.
Hosting sensitive workloads
This is the most popular use case. You can run your databases or internal business applications in private subnets where they have no access to the public internet. This is how government agencies host classified data and healthcare companies securely process personally identifiable information.
Hybrid and multi-cloud integration
You can securely link your VPC to the physical servers in your own office or even to a VPC at a different cloud provider. This approach, often called a hybrid cloud, uses a site-to-site VPN or a dedicated direct connection to integrate your on-premise and cloud resources into a single, unified network.
This is very useful for gradual migration. For example, you can keep your older, "legacy" applications running locally on your own hardware while building new, modern applications inside your VPC. It also lets you avoid vendor lock-in and use the best tools from each provider for specific tasks.
VPC architecture and pricing
When you design a VPC, the most common and secure approach is the three-tier architecture. It’s a standard for building secure applications, and it works by separating your application into three logical layers, or tiers.
Three-tier architecture in a VPC
This model separates your network based on the job each part does:
- Web tier: This is the only layer that faces the user; it runs in a public subnet and hosts your web servers.
- Application tier: This is the logic layer that processes information; it runs in a private subnet, hidden from the internet, and it only talks to the web tier.
- Database tier: This tier sits in its own private subnet and is highly secure, accessible only by the app tier.
Load balancers route traffic between the tiers, and firewalls protect each one. This design also lets you scale each part independently. For example, if you need more web servers, you can add them without touching the database.
Additional components and services
You can add other parts as your network grows, including:
- VPC endpoints: These let your private servers access other cloud services without using a NAT gateway or going over the public internet.
- VPC peering: This creates a direct, private connection between two VPCs.
- Transit gateway: If you have many VPCs, a transit gateway acts as a central hub to connect them all, which is simpler than managing many individual connections.
VPC pricing considerations
Creating the VPC container itself is almost always free, but you pay for the components you put inside it and the data you send.
- Components: You’re billed (usually hourly) for the virtual servers (instances) you run. You also pay for components like NAT gateways and any VPN connections.
- Data transfer: You’re often charged for data you send out of your VPC to the internet. Data going in is typically free. Using VPC endpoints, as mentioned above, can sometimes save you money on data transfer costs to other services.
All providers have different rates, so it's best to use their official pricing calculators to estimate your specific costs.
Setting up a virtual private cloud
Setting up a basic VPC involves a few key steps, and the process is similar across all major cloud providers. This is how it works:
- Log into your provider's console and choose a physical region (like US-East or Europe-West) where your network will live.
- Next, create the VPC by defining its private IP address range (like 10.0.0.0/16). This is the large block of internal-only addresses your whole network will use.
- After you've created the VPC, divide that large address range into smaller subnets. For example, you could make a public subnet for your web server and a separate private subnet for your database.
- Finally, configure your routing tables (the traffic rules) and gateways. You can attach an internet gateway to your public subnet for open access and set up a NAT gateway for your private subnets to allow secure outbound connections (like software updates). Then, launch your virtual servers into your subnets and apply security groups (your firewalls) to control exactly what traffic can get in or out.
Choosing the right cloud provider
All major providers offer VPCs, but your choice often depends on what your team already knows or what services you need. Here are some common options:
- AWS: Known for having the widest range of services.
- Google Cloud: Popular choice for its strengths in data analytics and machine learning.
- Microsoft Azure: A common pick for large businesses, especially those already using Windows Server and other Microsoft software.
Always use the provider's official pricing calculators to estimate your costs. Most also offer free tiers, so you can test the platform before committing.
Integration with on-premises infrastructure
If you’re a business owner, you’ll want to connect your new VPC to your existing office network. This hybrid setup is very common, and you can create it using a secure site-to-site VPN or by ordering a dedicated, private physical line from your provider.
Once connected, you can manage both your cloud and on-premise servers together. You can also integrate your company's user directory so employees can use single sign-on (SSO) across both networks.
Security considerations in a VPC
The best approach is to use layered defense, building security into the network, your servers, and your applications. A core principle for all security is least privilege, where you only grant the minimum access necessary for a person or a service to do its job.
Encryption and data protection
You should always encrypt your sensitive data, using:
- Encryption at rest: This scrambles your data when it's stored on a server (like on a virtual hard drive).
- Encryption in transit: This scrambles your data while it's moving over a network.
You can use the encryption keys provided by the cloud provider, or, for extra control, you can manage your own. You should also use VPC endpoints, which create a private connection from your VPC to other cloud services, so your data doesn’t have to travel over the public internet.
Identity and access management (IAM)
This is a critical layer: IAM is the service that lets you control who can do what inside your cloud account. It serves as the primary enforcement mechanism for zero-trust security. Instead of giving everyone full admin access, you create specific roles; for example, a developer might get read-only access to the live database, while a system administrator gets full permission to change network rules.
You should also add multi-factor authentication (MFA) for all your administrators. This requires another authentication factor in addition to a password, which provides a strong barrier against stolen credentials.
Best practices for regulatory compliance
If you handle sensitive information in industries like finance or healthcare, you need to prove you're following the rules. Make sure to:
- Audit regularly: Review your logs and security group rules to make sure nothing has changed.
- Segment your network: Use subnets to create separate, locked-down zones for data that falls under specific regulations (like credit card processing).
- Use tags: Label all your resources (like dev or production) so you can easily track them and generate reports.
- Follow a framework: You don't have to invent your security plan; use established guidelines, like those from NIST, to build your controls.
FAQ: Common questions about VPCs
What is the difference between a private cloud and a VPC?
The main difference is hardware. A private cloud uses dedicated physical servers you own or lease; this offers complete control but is expensive. A virtual private cloud (VPC) is a private, isolated network inside a public cloud, running on shared physical hardware. The provider manages the hardware, making the VPC more flexible and cost-effective.
What are the security benefits of using a VPC?
The main benefit is isolation. Your resources are hidden from the public internet by default, and you get complete control over all network traffic, using security groups to block unwanted access. This isolation makes it much easier to protect sensitive data and comply with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
How does VPC pricing compare to traditional hosting?
A virtual private cloud (VPC) uses a pay-as-you-go model. You only pay for the resources you use, which is usually cheaper than the traditional hosting model of buying your own servers (a large upfront cost). The main costs to watch are for components like Network Address Translation (NAT) gateways and the data you send out to the internet.
Can a VPC integrate with existing infrastructure?
Yes; you can securely connect your virtual private cloud (VPC) to your physical office network to create a hybrid cloud. This is usually done with a site-to-site VPN or a dedicated, private connection. This lets your cloud and office networks work together as a unified system.
Which industries benefit most from VPC solutions?
Any industry that handles sensitive data can benefit from virtual private cloud (VPC) solutions. This includes finance, healthcare, and government (which must meet strict regulatory requirements), retail (to secure payment processing), and tech companies (to create secure development and testing environments).
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN