How to implement zero trust

Zero trust represents a shift in how organizations protect what matters most. With cyber threats growing, adopting zero trust helps you stay ahead and protect your business from serious harm. The core idea of this security model is simple: never trust, always verify.
This guide shows how to implement zero trust from first scoping through daily upkeep. It weaves in network segmentation, microsegmentation, the principle of least privilege, and other proven moves.
Note: ExpressVPN provides consumer privacy tools, while zero trust is designed for enterprise security. We include this topic to help readers understand how zero trust is applied in organizations and its role in the wider cybersecurity and privacy landscape.
How to implement zero trust step by step
This five-step plan breaks the process into manageable stages, from initial discovery to continuous improvement.
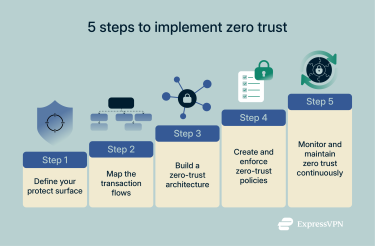
Step 1: Define your protect surface
You can’t protect what you don’t know. The first step is to identify your “protect surface.” That is, the critical assets that would cause maximum damage if compromised. Unlike the traditional concept of securing the entire threat surface, zero trust focuses on protecting the most valuable and sensitive resources. It typically includes:
- Business-critical data: Customer personally identifiable information (PII), financial records, intellectual property, and confidential business information.
- Mission-critical applications: Core business systems, databases, and revenue-generating applications.
- Essential services: Authentication systems, directory services, and other foundational IT infrastructure.
- High-value assets: Trade secrets, strategic plans, and competitive intelligence.
Keep this list slim; anything outside adds noise and cost. But think beyond data; consider assets whose compromise would lead to significant operational disruption, reputational harm, or financial loss. All subsequent steps will be about building controls to protect this specific surface.
Step 2: Map the transaction flows
Knowing what to protect gives you direction. The next task is to understand how information moves within your organization. How do employees, systems, or even outside partners access these vital assets? Where does data flow, and how do various apps interact?
For example, your finance team needs access to accounting software, but your marketing team does not. Here, diagrams can help. Map out who needs access, the routes data takes, and the connections between systems.
This mapping process often involves a combination of traffic analysis from your network tools, interviews with application owners and business unit leaders, and a review of existing process documentation.
By seeing these pathways clearly, you’ll spot exactly where to apply new security measures and how to design a network architecture that allows legitimate traffic while blocking everything else by default without disrupting how people get work done.
This map becomes the blueprint for your security policies.
Step 3: Build a zero-trust architecture
Now, put your strategy into practice by segmenting your network. Divide it into zones. Give each zone its own controls. This limits how far an intruder could go if one part of your system was compromised.
This is where zero-trust network access (ZTNA) solutions come into play. A ZTNA gateway creates secure, one-to-one connections between users and specific applications, effectively creating a microsegment of one for each access session.
Authentication sits at the heart of this approach. Use tools like multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM) to check credentials every time someone, or something, asks for access. Layer on firewalls and security brokers to watch and control every access point along the way.
Step 4: Create and enforce zero-trust policies
Zero-trust policies are the rules that govern how access decisions are made throughout your network. This step involves writing granular access rules that your segmentation gateways will enforce. Develop policies using the “5 Ws” framework:
- Who: Which users or entities are requesting access?
- What: Which applications or resources do they want to access?
- When: The time and context of the access request?
- Where: The location, device, and network from which access is requested?
- Why: The business justification for the access request?
For example, a policy might grant a specific accountant (Who) read-only access to the Q3 financial server (What) only from a corporate-managed laptop with up-to-date endpoint detection and response (EDR) software (Where), and only during standard business hours (When).
Step 5: Monitor and maintain zero trust continuously
A zero-trust implementation is not a one-time project; it is an ongoing process. The goal of this monitoring is twofold: to generate actionable alerts for your security operations team and to produce intelligence that helps you refine and strengthen your access policies over time.
Your segmentation gateways will produce a wealth of information about who is trying to access your resources. Analyzing this data helps you refine your policies, detect anomalies, and respond to potential attacks in real time.
You should use a security information and event management (SIEM) system to collect and analyze logs from all your security tools. This gives you a single view of your entire network. This continuous feedback loop allows you to adapt to new threats and changes in your business.
Security is never “done,” and this monitoring step ensures your zero-trust framework remains effective over the long term.
The 3 main principles of a zero-trust implementation
Zero trust stands on three simple ideas that change the way you keep your organization safe:
1. Never trust, always verify
This is the central idea of zero trust. It means you discard the old idea of a trusted internal network and an untrusted external network. Instead, you treat all access requests as untrusted until they are proven otherwise.
Every user, device, and application must be authenticated and authorized before being granted access to any resource, every single time. There are no trusted zones, only continuously verified connections.
2. Assume breach
A zero-trust strategy starts with the assumption that your network has already been compromised. This mindset changes how you design your security and takes you from prevention to limitation. Instead of focusing only on preventing attackers from getting in, you focus on limiting the damage they can do if they are already inside.
This is why microsegmentation is so important. By breaking your network into small, isolated segments, you prevent an attacker who compromises one part of the network from moving laterally to access your most sensitive data.
3. Enforce least-privilege access
The principle of least privilege dictates that users and applications should only be given the absolute minimum level of access they need to do their jobs, and nothing more. If a user only needs to read a file, they should not be given permission to edit or delete it.
This principle dramatically reduces your attack surface. If a user’s account is compromised, the attacker’s access is limited to that user’s very small set of permissions, preventing widespread damage.
Zero-trust deployment checklist
A zero-trust checklist can help you organize your project and make sure you cover all the necessary bases.
1. Define security goals and compliance needs
Before you start, you must clearly define what you want to achieve with your zero-trust implementation. Your goals will guide your priorities and help you measure success. Are you trying to better protect specific data to meet compliance regulations like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA)? Is your main objective to secure a remote workforce? Or are you focused on preventing lateral movement by attackers inside your network?
Knowing your specific goals helps you focus your efforts where they will have the most impact.
2. Involve key stakeholders and decision-makers
Implementing zero trust is a significant change that affects the entire organization, not just the IT department. You need strong support from leadership to secure the budget and authority required for such a project. It is important to involve key stakeholders from IT, security, and various business departments from the very beginning.
When everyone understands the goals and benefits of the project, the transition becomes much smoother. This top-down support is fundamental for success and helps align the entire organization behind the new security strategy.
3. Assess tooling and infrastructure readiness
Next, you need to review your current technology stack to see if it can support a zero-trust model. Do you have a centralized identity provider? Do your EDR tools provide device health telemetry? Can your network hardware or firewalls support microsegmentation? This identifies the technical gaps you need to fill.
You will likely need to invest in or upgrade some of your existing security solutions, such as adding MFA across all systems, deploying EDR tools, or implementing next-generation firewalls capable of microsegmentation. This assessment helps you identify gaps and plan your technology investments.
4. Set up metrics and monitoring systems
You can’t improve what you can’t measure. Define how you will track the success of your zero-trust strategy.
Key performance indicators might include a reduction in security incidents, faster threat detection times, or the percentage of applications and users covered by zero-trust policies. Key risk indicators could track things like the number of lateral movement attempts blocked.
You must set up your monitoring systems, like a SIEM, to track these metrics from day one. This data will prove the value of the project and help you refine your policies over time.
5. Provide team training and support cultural change
Zero trust is a new way of thinking about security, moving from a model of implicit trust to one of explicit verification. Teach everyone across all roles what they must do differently and why it helps. Ongoing support and accessible help make the change stick. This will require a cultural shift, though.
Be prepared to manage this change by communicating clearly and often. When employees understand that the changes are designed to protect the company and their own data, they are more likely to become active participants in the security process rather than seeing it as a roadblock.
Tool and vendor evaluation guide
Selecting the right zero-trust tools and vendors is critical for implementation success. Picking the right tools begins with your real-world needs: Choose solutions that follow National Institute of Standards and Technology (NIST) 800-207 (the official guidance for zero-trust architecture) and provide seamless integration across identity, access controls, and network security. Evaluate these solutions based on specific criteria:
- Integration capabilities: Does the tool integrate with your existing identity provider (like Okta or Azure AD) and security tools (like your SIEM and EDR)?
- Policy granularity: How specific can the access rules be? Can you define policies based on user role, device health, location, and time of day?
- Scalability and performance: Can the solution handle your organization’s traffic load without introducing latency that disrupts user experience?
- Vendor support and roadmap: Does the vendor have a clear vision for the product’s future and a strong reputation for customer support?
Finally, cover the endpoints with monitoring and automated response and add cloud and secure access service edge (SASE) solutions to manage risk across your digital footprint. Ultimately, select options that work together, can grow with your business, and provide reliable support when questions arise.
Is zero trust difficult to implement?
Implementing zero trust takes effort, but it’s very achievable with the right plan and support.
Common technical challenges
These difficulties usually fall into two main categories: technical and organizational. On the technical side, many organizations struggle with legacy systems. Older hardware and software applications were often built for a different era of security and may not support modern authentication methods or the APIs needed for a dynamic zero-trust environment.
Another technical issue is the sheer complexity of modern IT infrastructure. With assets spread across on-premise data centers and multiple cloud providers, getting a complete and accurate picture of all users, devices, and data flows can be a significant undertaking.
Resource constraints such as budget limitations, skilled personnel shortages, and competing IT priorities can also slow or derail zero-trust initiatives.

Overcoming mindset and culture barriers
People naturally hesitate to change, especially when it comes to how they work. Employees may be used to having broad access to network resources and may see new security steps as an inconvenience.
Leaders need to communicate the “why” behind the changes clearly. Explaining that the goal is to protect the company’s data and their own information can help get everyone on board. Leadership support is fundamental to driving this cultural shift.
Tips to simplify adoption
To make your zero-trust implementation smoother, start small. For example, start where you’ll see the most benefit quickly, such as protecting your most sensitive assets or users with the broadest access.
Build on your existing investments and expand in stages. Automate as much as possible to save time and reduce mistakes. If expert support is needed, don’t hesitate to bring in partners; this helps move the process along and builds internal confidence for the next steps.
FAQ: Common questions about implementing zero trust
What are the seven pillars of zero trust?
While our five-step roadmap provides a process for implementation, the zero-trust architecture itself is built upon seven foundational pillars, as defined by the U.S. Department of Defense:
- User (verify identity and enforce access controls).
- Device (assess device security before granting access).
- Network/Environment (segment and monitor traffic to limit threats).
- Application/Workload (restrict access and secure app behavior).
- Data (protect data at rest, in transit, and in use).
- Visibility and Analytics (monitor activity and detect anomalies).
- Automation and Orchestration (automate threat response and policy enforcement).
Together, they ensure that trust is never assumed and is continuously verified.
What budget should I plan for a zero-trust rollout?
There is no single answer for a zero-trust budget. The cost depends on the size of your organization and the state of your current infrastructure. For many, zero trust is more about reallocating existing security funds and replacing older, less effective tools with modern solutions that support the framework. The key is to start with a clear plan and prioritize spending on the areas that will reduce the most risk.
Which tools support zero-trust implementation?
No single tool provides a complete zero-trust solution. You’ll need a combination of zero-trust tools that work together. Key categories include identity and access management (IAM) platforms with multi-factor authentication (MFA); endpoint detection and response (EDR) tools to secure devices; next-generation firewalls and other gateways for microsegmentation; and secure remote access solutions to encrypt traffic and enforce policies for remote and mobile users.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN